The core of Tera Term is written on C++. This should not cause a problem for those who only knows C language because the syntax of both languages is very close. Microsoft Visual C++ (VC++) supports the original ANSI C standard (C89) and does not support newer standard C99. VC++ has its own implementation of C99-like functions. The names of these functions start with underscore (_), which makes it easy to identify them. For example, the _snprintf() of VC++ is different from the snprintf() of ANSI C(C99).
CygTerm is written in C language and should be compiled using gcc compiler included in Cygwin package.
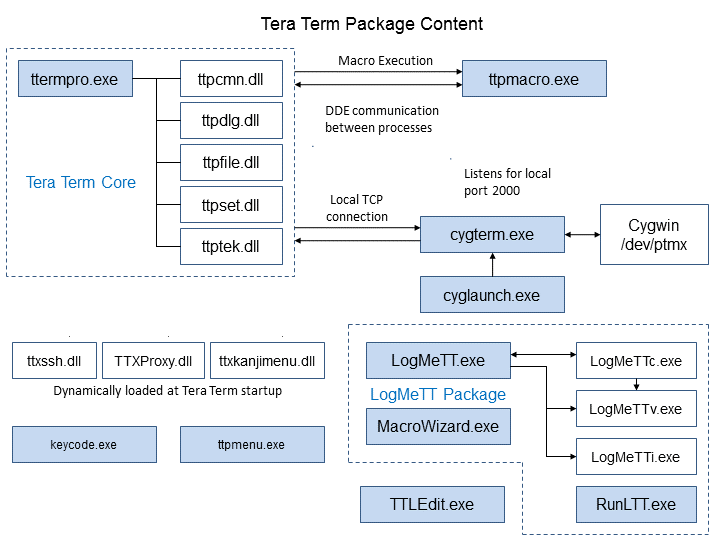
It is inefficient to build advanced software from scratch, that's why Tera Term actively uses open source libraries. This, however, requires from developers to be careful and avoid license violations, especially GPL.
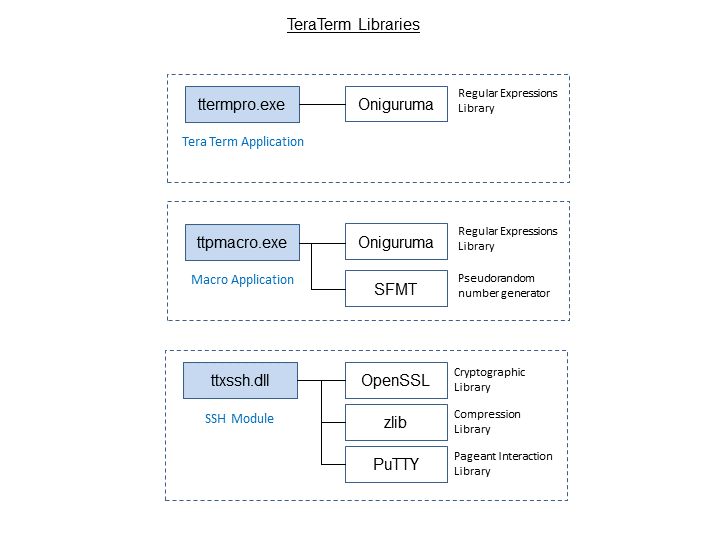
Several Tera Term modules are linked to open source libraries as shown on the drawing below.
The macro program is linked to regular expression library "Oniguruma", which allows to handle regular expressions in "waitregex", "strmatch" and "strreplace" macro commands.
Tera Term also calls this library to display Oniguruma version information in "About Tera Term" dialog box.
The macro program is linked to pseudorandom number generator "SFMT", which allows to generate random number in "random" macro command.
"TTSSH" module is linkd to "OpenSSL" library to perform cryptography related operations. One may think that OpenSSL library contains only Secure Socket Layer (SSL) protocol related functions used for secure web access, however that is wrong assumption. OpenSSL library also supports basic cipher algorithms, which are utilized by "TTSSH" module. Since Secure Layer related functions of the library are not used, it is very unlikely that "TTSSH" module will be compromised if a SSL related security hole is found in OpenSSL library.
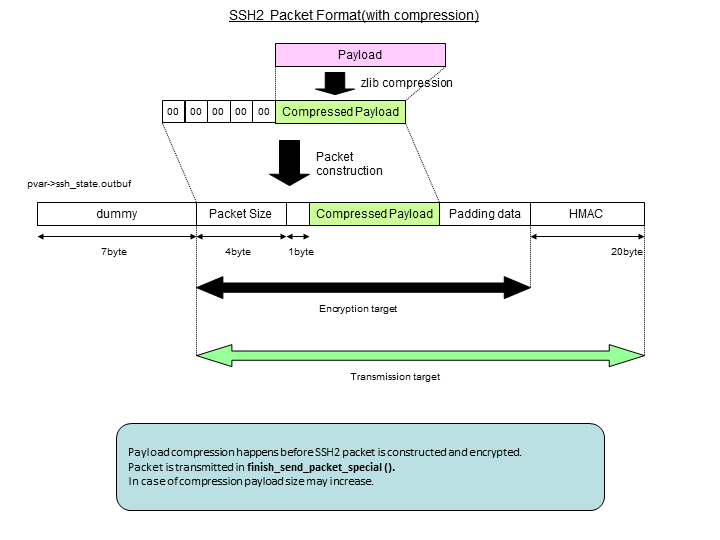
"TTSSH" module is linkd to compression Library "zlib" to compress SSH packets. Packet compression is effective on low speed networks like for example with dial-up connections, however in high speed networks it may slow down communication. That's why packet compression function is disabled by default.
"TTSSH" module is linkd to terminal emulator "PuTTY." PuTTY package contains SSH authentication agent called "Pageant". TTSSH uses part of PuTTY source code to support Pageant based authentication method. Communication part and terminal emulation part of PuTTY source code is not used.
Note that these libraries are called statically (not via dynamic link). When compiling the source code with these libraries use "/MT" option. Tera Term doesn't use dynamic calls to the libraries because not all user environments can support such calls, which may cause Tera Term to crash.
| Module | Order |
|---|---|
| TTProxy | 0 |
| TTSSH | 2500 |
| TTX Kanji Menu | 5000 |
static TTXExports Exports = {
/* This must contain the size of the structure. See below for its usage. */
sizeof(TTXExports),
/* This is the load order number of this DLL. */
ORDER,
/* Now we just list the functions that we've implemented. */
TTXInit,
NULL, /* TTXGetUIHooks */
NULL, /* TTXGetSetupHooks */
NULL, /* TTXOpenTCP */
NULL, /* TTXCloseTCP */
NULL, /* TTXSetWinSize */
TTXModifyMenu,
TTXModifyPopupMenu,
TTXProcessCommand,
NULL, /* TTXEnd */
NULL /* TTXSetCommandLine */
};
The export function of the plug-in module should be designed in such a way that it does not interfere with other plug-ins. Also, when the plug-in module is called by Tera Term core, the module needs to check whether the request was sent to it, or to another module.
| Function | Description |
|---|---|
| TTXBind | This function is called at first. The function sends export function structure to Tera Term core. |
| TTXInit | This function is called right after TTXBind(). The function receives global variables (ts and cv) from Tera Term core and initialized plug-in module. |
| TTXGetUIHooks | This function can hook a dialog handle. The function is used to change the dialog interface of Tera Term. The hook targets are: &SetupTerminal, &SetupWin, &SetupKeyboard, &SetupSerialPort, &SetupTCPIP, &GetHostName, &ChangeDirectory, &AboutDialog, &ChooseFontDlg, &SetupGeneral, &WindowWindow |
| TTXGetSetupHooks | This function can hook to setup routine. The hooked function should call the original function. When several plug-in modules exist, each function is called in accordance with order number. The hook targets are: &ReadIniFile, &WriteIniFile, &ReadKeyboardCnf, &CopyHostList, &AddHostToList, &ParseParam |
| TTXOpenTCP | This function is called only for TCP connections; it should not be used for Serial connections. The function can hook to the socket interfaces: &Pclosesocket, &Pconnect, &Phtonl, &Phtons, &Pinet_addr, &Pioctlsocket, &Precv, &Pselect, &Psend, &Psetsockopt, &Psocket, &PWSAAsyncSelect, &PWSAAsyncGetHostByName, &PWSACancelAsyncRequest, &PWSAGetLastError |
| TTXCloseTCP | This function is called only for TCP connections; it should not be used for Serial connections. If there is a hook to one of the following socket interfaces, the function must restore the original interface prior to exit: &Pclosesocket, &Pconnect, &Phtonl, &Phtons, &Pinet_addr, &Pioctlsocket, &Precv, &Pselect, &Psend, &Psetsockopt, &Psocket, &PWSAAsyncSelect, &PWSAAsyncGetHostByName, &PWSACancelAsyncRequest, &PWSAGetLastError |
| TTXSetWinSize | This function is called when the terminal screen is resized. |
| TTXModifyMenu | This function is called when Tera Term menu is initialized. The function allows to insert new menu item into original Tera Term menu. |
| TTXModifyPopupMenu | This function is called when Tera Term pop-up menu is initialized. The function can add new pop-up menu item to the original pop-up menu. |
| TTXProcessCommand | This function is called when Tera Term menu is executed. The function can process the plug-in module menu. |
| TTXEnd | This function is called when Tera Term exits. |
| TTXSetCommandLine | This function is called when the command line parameter is processed during set up of new connection and also while duplicating existing connection. The original parameter of plug-in module is processed. |
ts->ConfirmChangePaste = GetOnOff(Section, "ConfirmChangePaste", FName, TRUE);Use WriteIniFile()#ttset.c to write into .ini file.
WriteOnOff(Section, "ConfirmChangePaste", FName, ts->ConfirmChangePaste);To read or write string entries use GetPrivateProfileString() and WritePrivateProfileString() Win32 API functions. For integer values use GetPrivateProfileInt() and WriteInt() from Win32 API.
| Old | New |
|---|---|
| sprintf(), _snprintf() | _snprintf_s() |
| strcat(), strncat() | strncat_s() |
| strcpy(), strncpy() | strncpy_s() |
An example of strncpy_s() function use is shown below. The second argument (numberOfElements) specifies the buffer size including terminating null (\0). Since the write buffer size is only three bytes, five bytes of data specified in the third argument (strSource) are truncates down to two bytes and null is added to the end. After executing these commands buf[] will contain the string "he\0".
char buf[3]; strncpy_s(buf, sizeof(buf), "hello", _TRUNCATE);Below is an example of using strncat_s() function. The first argument (strDest) of strncat_s() function must have terminating null to concatenate strings. The second argument (numberOfElements) is specified with the buffer size that includes terminating null. In this example, when the first strncat_s() function is executed, five bytes (four chars + null) will be stored in str[]. When the second strncat_s() is executed, only two chars will be copied into the buffer, because there are only two free bytes remaining. After executing below code the buffer will contain "TeraTe\0" (4 chars + 2 chars + null).
char str[7]; str[0] = '\0'; strncat_s(str, sizeof(str), "Tera", _TRUNCATE); strncat_s(str, sizeof(str), "Term", _TRUNCATE);The final example demonstartes the use of _snprintf_s() function. Don't confuse this function with _snprintf() that doesn't add terminating null to the buffer. After execution of the code shown below buf[] will contain "ab\0".
char buf[3]; _snprintf_s(buf, sizeof(buf), _TRUNCATE, "abcdef");
static BOOL MySetLayeredWindowAttributes(HWND hwnd, COLORREF crKey, BYTE bAlpha, DWORD dwFlags)
{
typedef BOOL (WINAPI *func)(HWND,COLORREF,BYTE,DWORD);
static HMODULE g_hmodUser32 = NULL;
static func g_pSetLayeredWindowAttributes = NULL;
if (g_hmodUser32 == NULL) {
g_hmodUser32 = LoadLibrary("user32.dll");
if (g_hmodUser32 == NULL)
return FALSE;
g_pSetLayeredWindowAttributes =
(func)GetProcAddress(g_hmodUser32, "SetLayeredWindowAttributes");
}
if (g_pSetLayeredWindowAttributes == NULL)
return FALSE;
return g_pSetLayeredWindowAttributes(hwnd, crKey,
bAlpha, dwFlags);
}
The downside of this approach is - too much work creating prototypes for every function that will be used. The easier way to achieve the same result is to use a mechanism called "lazy loading DLL". If the function you want to use is not supported by older Windows version, you can specify it in Visual Studio project settings; mark the function as lazy loaded DLL.
Currently Tera Term can run on Windows 95 despite the fact that it is compiled using Visual Studio 2005. The binary program built by Visual Studio 2005 by default contains link to IsDebuggerPresent function. This causes program to fail under Windows 95 because this function was first introduced in Windows 98. To resolve this issue dummy symbol replacing IsDebuggerPresent function was defined. This is certainly "unofficial" method not supported by Microsoft. For more details please check the header file comapt_w95.h.
void OutputDebugPrintf(char *fmt, ...) {
char tmp[1024];
va_list arg;
va_start(arg, fmt);
_vsnprintf_s(tmp, sizeof(tmp), _TRUNCATE, fmt, arg);
OutputDebugString(tmp);
}
#ifdef _DEBUG _CrtSetDbgFlag(_CRTDBG_ALLOC_MEM_DF | _CRTDBG_LEAK_CHECK_DF); #endifIt should be noted that Windows allocates separate virtual memory region for each running process. If program ends and leaves unreleased memory, operating system will still release it.
| Generating point | Source file |
|---|---|
| Serial connection | CommStart()#commlib.c |
| TELNET keep-alive | TelStartKeepAliveThread()#telnet.c |
| IPv4/v6 socket creation | WSAAsyncGetAddrInfo()#WSAAsyncGetAddrInfo.c |
| Generating point | Source file |
|---|---|
| SSH keep-alive | start_ssh_heartbeat_thread()#ssh.c |
| SCP sending | SSH2_scp_tolocal()#ssh.c |
| SCP receiving | SSH2_scp_fromremote()#ssh.c |
#define WM_SEND_HEARTBEAT (WM_USER + 1)
static INT_PTR CALLBACK telnet_heartbeat_dlg_proc(HWND hWnd, UINT msg, WPARAM wp, LPARAM lp)
{
switch (msg) {
case WM_INITDIALOG:
return FALSE;
case WM_SEND_HEARTBEAT:
TelSendNOP();
return TRUE;
break;
case WM_COMMAND:
break;
case WM_CLOSE:
return TRUE;
case WM_DESTROY:
return TRUE;
default:
return FALSE;
}
return TRUE;
}
static unsigned _stdcall TelKeepAliveThread(void *dummy) {
static int instance = 0;
if (instance > 0)
return 0;
instance++;
while (cv.Open && nop_interval > 0) {
if (time(NULL) >= cv.LastSendTime + nop_interval) {
SendMessage(keepalive_dialog, WM_SEND_HEARTBEAT, 0, 0);
}
Sleep(100);
}
instance--;
return 0;
}
void TelStartKeepAliveThread() {
unsigned tid;
if (ts.TelKeepAliveInterval > 0) {
nop_interval = ts.TelKeepAliveInterval;
keepalive_dialog = CreateDialog(hInst, MAKEINTRESOURCE(IDD_BROADCAST_DIALOG),
HVTWin, telnet_heartbeat_dlg_proc);
keepalive_thread = (HANDLE)_beginthreadex(NULL, 0, TelKeepAliveThread, NULL, 0, &tid);
if (keepalive_thread == 0) {
keepalive_thread = INVALID_HANDLE_VALUE;
nop_interval = 0;
}
}
}
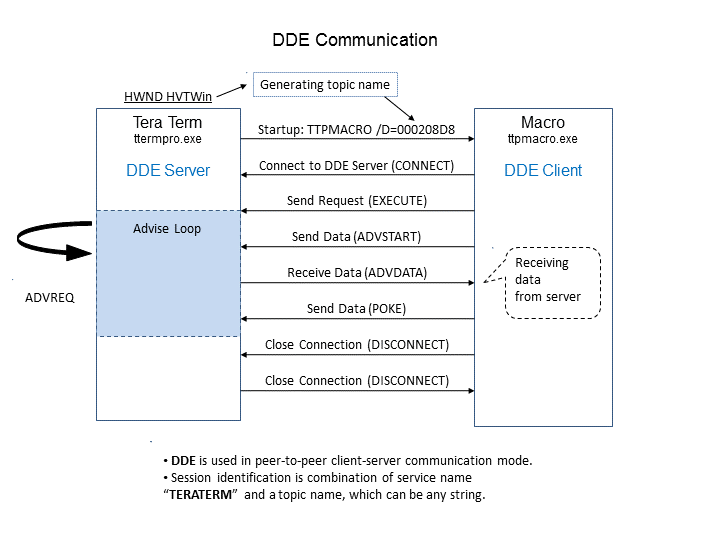
DDE communication is similar to TCP - both protocols allow to open peer-to-peer, client-server connection. Applications can establish DDE connectivity by calling functions from Dynamic Data Exchange Management Library (DDEML). Calls to DDEML functions are done the same way as the calls to Win32 API functions.
| Type | Description |
|---|---|
| XTYP_ADVREQ | Informs the server that an advise transaction is outstanding for the specific topic name. The system sends this transaction to DDE callback function DdeCallback, then the server calls the DdePostAdvise function. |
| XTYP_POKE | DDE client uses XTYP_POKE transaction to send unsolicited data to the server. |
| XTYP_ADVSTART | Advise loop starts on the DDE server. |
| XTYP_ADVDATA | Informs periodically the client that the value of the data item has changed. |
| XTYP_EXECUTE | DDE client uses XTYP_EXECUTE transaction to send a command string to the server. |
| Function | Description |
|---|---|
| DdeInitialize | Initializes DDE and registers callback function. If the function succeeds, it returns DMLERR_NO_ERROR. |
| DdeCreateStringHandle | Creates a handle for a string. The handle is used for communication between the server and the client. |
| DdeNameService | Registers or unregisters the service name "TERATERM" in DDE server. If the registration succeeds, the XTYP_REGISTER transaction is send to the DDE client. |
| DdeCmpStringHandles | Compares two string handles. |
| DdeClientTransaction | Sends a transaction from the client to the server. Type of transactions can be specified. Examples of transaction types are: XTYP_REQUEST, XTYP_EXECUTE, XTYP_ADVSTART, XTYP_POKE. Timeout value can be set to define the maximum amount of time in milliseconds that the client will wait for a response (ACK) from the server. Tera Term uses timeout value of 5000 milliseconds (5 seconds). |
| DdeAccessData | Provides access to the data in the specified DDE object. An application must call the DdeUnaccessData function when it has finished accessing the data in the object. |
| DdeCreateDataHandle | Creates the DDE object and returns the handle. The handle is used for the DDE server's advise loop, also to send data to DDE client when XTYP_REQUEST transaction is received. |
| DdeGetData | Copies data from the specified DDE object to the specified local buffer. |
| DdeDisconnect | Terminates DDE communication. |
| DdePostAdvise | Causes the system to send XTYP_ADVREQ transaction to the calling (server) application's DDE callback function for each client with an active advise loop on the specified topic and item. A server application should call this function whenever the data associated with the topic name or item name pair changes. |
SetTopic(); if (! InitDDE()) return; strncpy_s(Cmnd, sizeof(Cmnd),"TTPMACRO /D=", _TRUNCATE); strncat_s(Cmnd,sizeof(Cmnd),TopicName,_TRUNCATE);Every time a transaction is sent from DDE client to DDE sever DdeCallbackProc callback function is being executed. The callback function is registered during DDE initialization with DdeInitialize().
ConvH = DdeConnect(Inst, Service, Topic, NULL);
if (ConvH == 0) return FALSE;
Linked = TRUE;
Cmd[0] = CmdSetHWnd;
w = HIWORD(HWin);
Word2HexStr(w,&(Cmd[1]));
w = LOWORD(HWin);
Word2HexStr(w,&(Cmd[5]));
DdeClientTransaction(Cmd,strlen(Cmd)+1,ConvH,0,
CF_OEMTEXT,XTYP_EXECUTE,1000,NULL);
DdeClientTransaction(NULL,0,ConvH,Item,
CF_OEMTEXT,XTYP_ADVSTART,1000,NULL);


buffer_t *msg;
int len;
char *s;
unsigned char *outmsg;
msg = buffer_init();
if (msg != NULL) {
buffer_put_int(msg, SSH2_DISCONNECT_PROTOCOL_ERROR);
s = "disconnected by server request";
buffer_put_string(msg, s, strlen(s));
s = "";
buffer_put_string(msg, s, strlen(s));
len = buffer_len(msg);
outmsg = begin_send_packet(pvar, SSH2_MSG_DISCONNECT, len);
memcpy(outmsg, buffer_ptr(msg), len);
finish_send_packet(pvar);
buffer_free(msg);
}
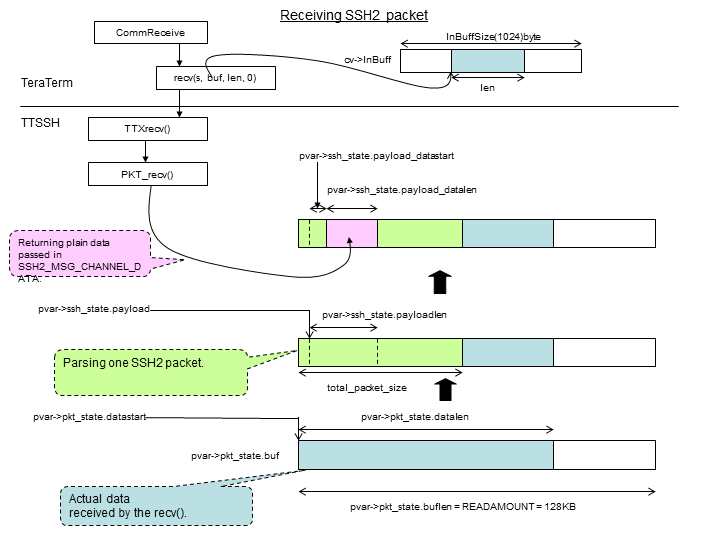
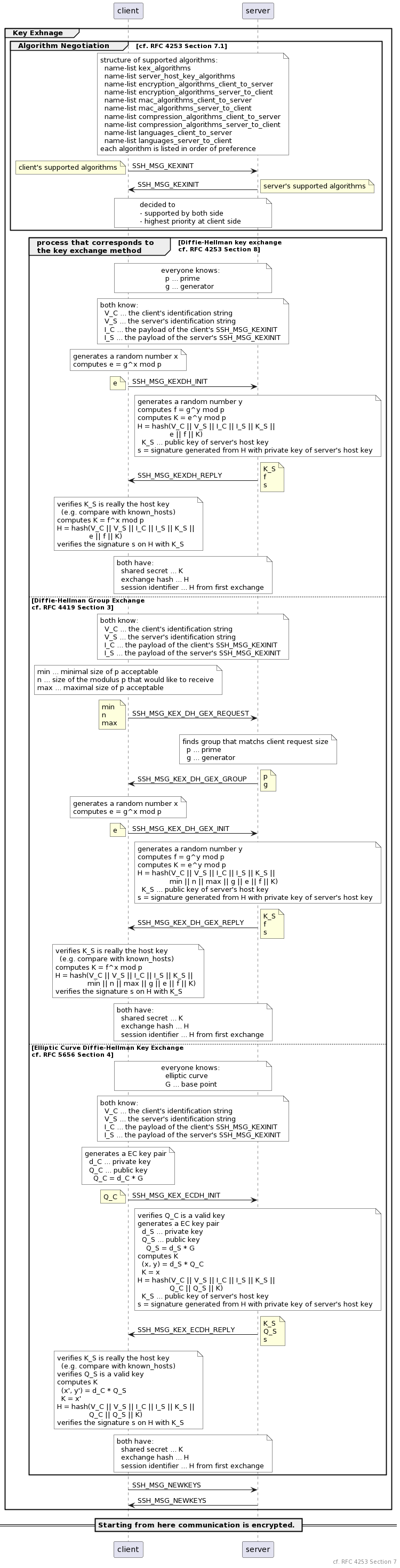
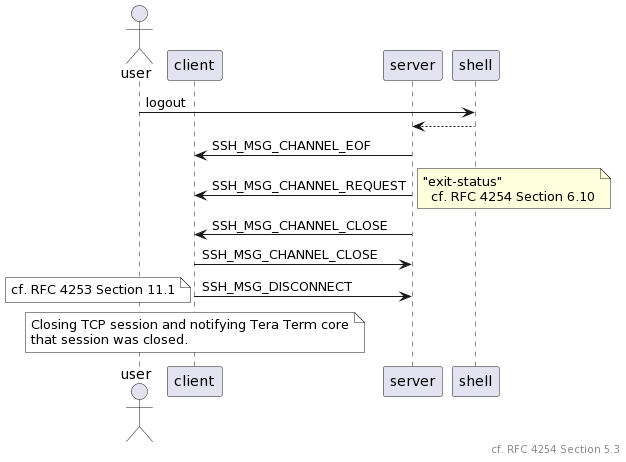
Once ready, SSH packet is sent by finish_send_packet_special() function, which is called from finish_send_packet(). Format of transmitted packet is shows below. Before encrypting the packet using symmetric key, we must create header and footer. 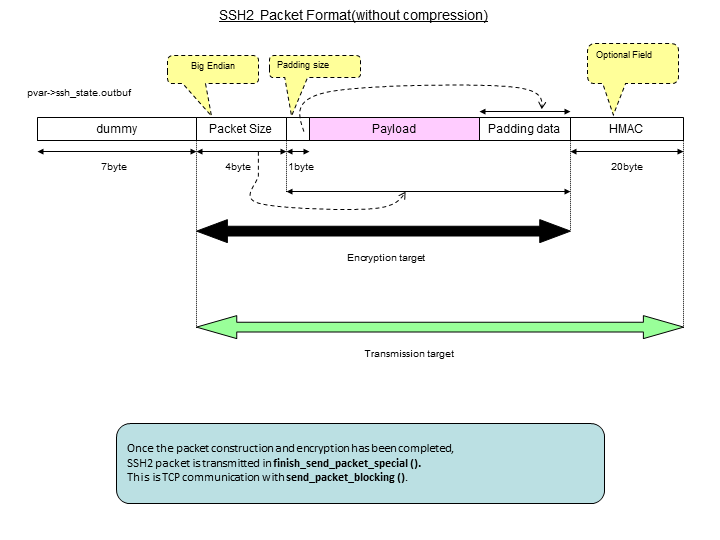



SCP via SSH2
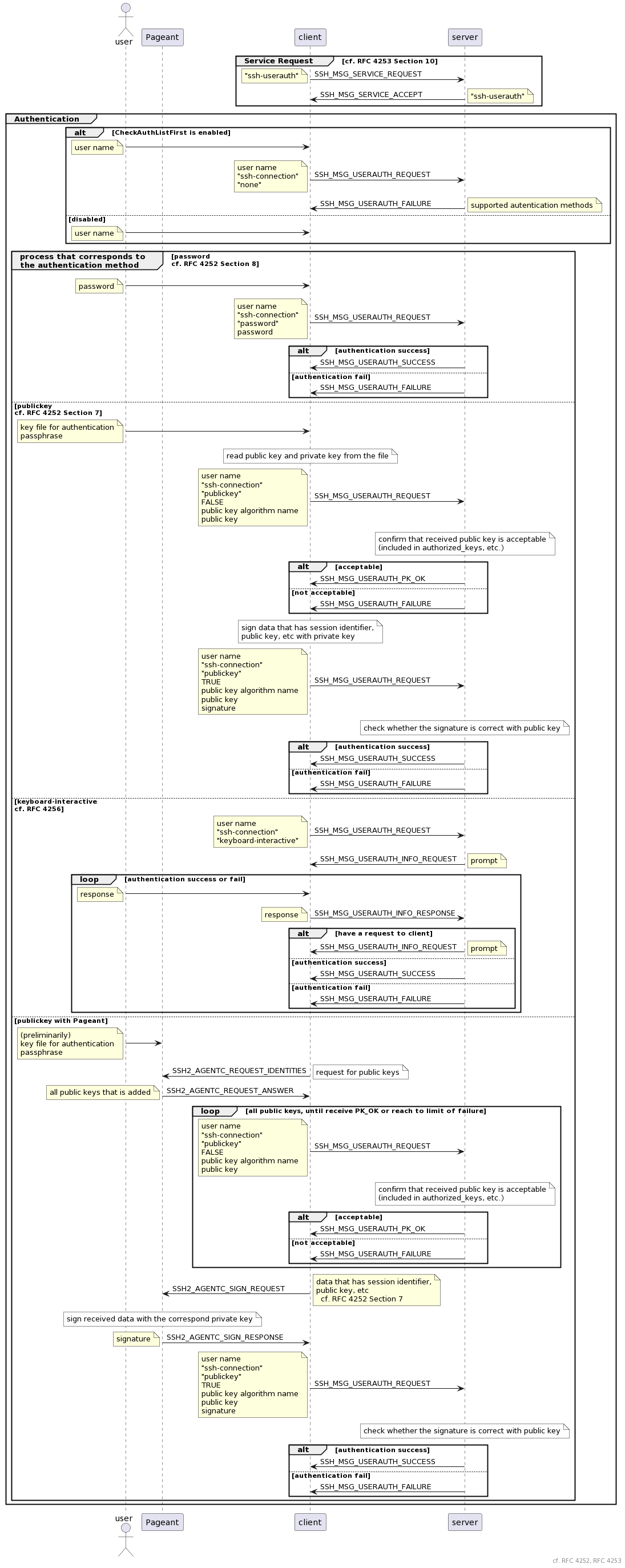
When you send SSH2_MSG_CHANNEL_REQUEST message to the server, you can run an external command by specifying the service name "exec" instead of "pty-req".
After successful user authentication
----> SSH2_MSG_CHANNEL_OPEN(90)
<---- SSH2_MSG_CHANNEL_OPEN_CONFIRMATION(91)
----> SSH2_MSG_CHANNEL_REQUEST(98) external command sent in the service name "exec" ("scp -f")
<---- SSH2_MSG_CHANNEL_WINDOW_ADJUST (remote_window+=131072 bytes)
<---- SSH2_MSG_CHANNEL_EXTENDED_DATA (local_window-=36 bytes)
<---- SSH2_MSG_CHANNEL_DATA(94)
SCP via SSH1
Sending SSH_CMSG_EXEC_CMD to the server allows to run an external command during SSH1 session.External command has the following format:
* "scp [-v] [-r] [-p] [-d] -t file name" ;copy Local-to-Remote
* "scp [-v] [-r] [-p] [-d] -f file name" ;copy Remote-to-Local
-v verbose
-r recursive
-p keep time stamp
-d directory
-t copy Local-to-Remote
-f copy Remote-to-Local
Data Transfer
As soon as transmission of external command has been completed, we can start sending or receiving the file content.
1. File Sending Flow
<---- Send timestamp (optional)
<---- Send "C0664 file_size filename" ; 664 in this example is file permission at destination
<---- Send content of the file
<---> Close session
2. File Receiving Flow
----> Receive timestamp (optional)
<---- Send 0
----> Receive "C0664 file_size filename"
<---- Send 0
----> Receive content of the file
----- Set file timestamp (optional)
<---- Send 0
<---> Close session
Note
When file name contains full path, forward slash ("/") must be used as directory separator. Backslashes ("\") are not supported and should be replaced with forward slashes.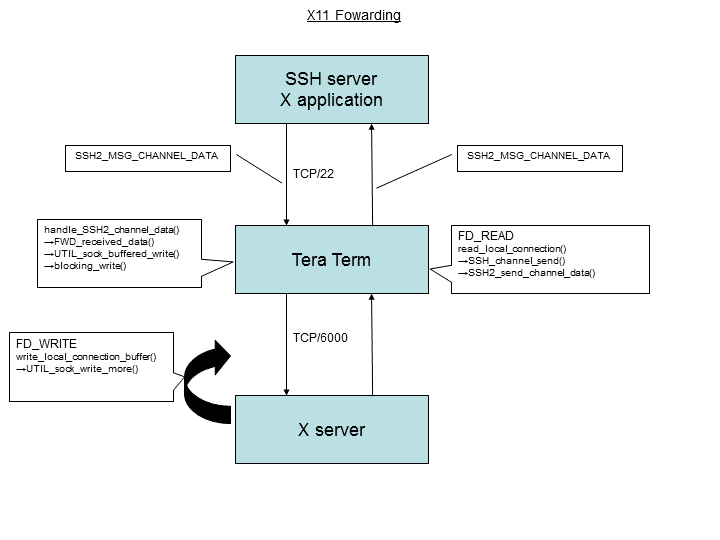
[TTSSH] DefaultForwarding=XOn the server side, in case of using OpenSSH, X11Forwarding value needs to be set to "yes" in "sshd_config" file. Default value is "no", which disables support of X11 forwarding.
X11Forwarding=yesWhen X11 forwarding is enabled, Tera Term sets request type to "FWD_REMOTE_X11_TO_LOCAL". This means the forwarding will be performed from SSH server towards Tera Term. After opening the session, Tera Term sends "SSH2_MSG_CHANNEL_OPEN_CONFIRMATION" message to the remote host to initialize X11 transfer.
if (c->type == TYPE_SHELL) {
// Preparing port forwarding (2005.2.26, 2005.6.21 yutaka)
// X11 request must be issued after opening the shell (2005.7.3 yutaka)
FWD_prep_forwarding(pvar);
FWD_enter_interactive_mode(pvar);
}
FWD_prep_forwarding() function sends "x11-req" service name and "MIT-MAGIC-COOKIE-1" to SSH server. This initializes X11 forwarding on the server. After completing initialization of X11 server will automatically set environment variable "DISPLAY".
# echo $DISPLAY DISPLAY=localhost:10.0When local PC is ready, user can activate X application on SSH server. The server sends X application data to Tera Term in SSH2_MSG_CHANNEL_DATA message format. This data is processed by FWD_received_data() function, which then forwards it to X server (TCP/6000). X server will receive the data in channel->local_socket and will treat it in non-blocking mode. Furthermore, since not all packets may be sent at once, prior to being processed further, the data must be accumulated in an internal buffer. Once channel->local_socket receives the data it sends out FD_WRITE message and calls write_local_connection_buffer() function. If there is a data in the buffer that has not been sent the last time, it will be read from the buffer and another attempt will be made to send it.
#define MAXNESTLEVEL 10 /* defines the maximum number of nested files (up to nine includes) */ static int INest; /* current nested number */ static HANDLE BuffHandle[MAXNESTLEVEL]; /* buffer handle received from GlobalAlloc () */ static PCHAR Buff[MAXNESTLEVEL]; /* buffer area */ static BINT BuffLen[MAXNESTLEVEL]; /* file size (buffer size) */ static BINT BuffPtr[MAXNESTLEVEL]; /* offset of buffer (read position) */
| Condition | Handling |
|---|---|
| TTLStatus==IdTTLEnd | Ends the macro program |
| Unhandled Data (OutLine>0) | Sends data to Tera Term core |
| TTLStatus==IdTTLRun | Run the macro line by line |
| TTLStatus==IdTTLWait | Waits ('wait' command) |
| TTLStatus==IdTTLWaitLn | Waits ('waitln' command) |
| TTLStatus==IdTTLWaitNL | Receives line ('recvln' command) |
| TTLStatus==IdTTLWait2 | Waits for string ('waitrecv' command) |
char LineBuff[MaxLineLen]; /* one row can store up to 500 bytes */ WORD LinePtr; /* buffer offset */ WORD LineLen; /* buffer size */ExecCmnd() function called from Exec() performs lexical analysis of the commands. Lexical analysis is done by simple string search within LineBuff[], one byte at a time. High level description of the analysis algorithm is shown below.
The system provides one caret per queue. A window should create a caret only when it has the keyboard focus or is active. The window should destroy the caret before losing the keyboard focus or becoming inactive.Above requirement means that CreateCaret() can be called only when the window is active and DestroyCaret() should be called before the window becomes inactive.
void CaretKillFocus(BOOL show)
{
int CaretX, CaretY;
POINT p[5];
HPEN oldpen;
HDC hdc;
DispInitDC();
hdc = VTDC;
CaretX = (CursorX-WinOrgX)*FontWidth;
CaretY = (CursorY-WinOrgY)*FontHeight;
p[0].x = CaretX;
p[0].y = CaretY;
p[1].x = CaretX;
p[1].y = CaretY + FontHeight - 1;
if (CursorOnDBCS)
p[2].x = CaretX + FontWidth*2 - 1;
else
p[2].x = CaretX + FontWidth - 1;
p[2].y = CaretY + FontHeight - 1;
if (CursorOnDBCS)
p[3].x = CaretX + FontWidth*2 - 1;
else
p[3].x = CaretX + FontWidth - 1;
p[3].y = CaretY;
p[4].x = CaretX;
p[4].y = CaretY;
if (show) { // Show polygon cursor (non-focused)
oldpen = SelectObject(hdc, CreatePen(PS_SOLID, 0, ts.VTColor[0]));
} else {
oldpen = SelectObject(hdc, CreatePen(PS_SOLID, 0, ts.VTColor[1]));
}
Polyline(VTDC, p, 5);
oldpen = SelectObject(hdc, oldpen);
DeleteObject(oldpen);
DispReleaseDC();
}
if (((h = GetModuleHandle("kernel32.dll")) != NULL) &&
(GetProcAddress(h, "QueryDosDeviceA") != NULL) &&
(QueryDosDevice(NULL, devicesBuff, 65535) != 0)) {
p = devicesBuff;
while (*p != '\0') {
if (strncmp(p, "COM", 3) == 0 && p[3] != '\0') {
ComPortTable[comports++] = atoi(p+3);
if (comports >= ComPortMax)
break;
}
p += (strlen(p)+1);
}
static void ListupSerialPort(LPWORD ComPortTable, int comports, char **ComPortDesc, int ComPortMax)
{
GUID ClassGuid[1];
DWORD dwRequiredSize;
BOOL bRet;
HDEVINFO DeviceInfoSet = NULL;
SP_DEVINFO_DATA DeviceInfoData;
DWORD dwMemberIndex = 0;
int i;
DeviceInfoData.cbSize = sizeof(SP_DEVINFO_DATA);
bRet =
SetupDiClassGuidsFromName(_T("PORTS"), (LPGUID) & ClassGuid, 1,
&dwRequiredSize);
if (!bRet) {
goto cleanup;
}
DeviceInfoSet =
SetupDiGetClassDevs(&ClassGuid[0], NULL, NULL, DIGCF_PRESENT | DIGCF_PROFILE);
if (DeviceInfoSet) {
dwMemberIndex = 0;
while (SetupDiEnumDeviceInfo
(DeviceInfoSet, dwMemberIndex++, &DeviceInfoData)) {
TCHAR szFriendlyName[MAX_PATH];
TCHAR szPortName[MAX_PATH];
DWORD dwReqSize = 0;
DWORD dwPropType;
DWORD dwType = REG_SZ;
HKEY hKey = NULL;
bRet = SetupDiGetDeviceRegistryProperty(DeviceInfoSet,
&DeviceInfoData,
SPDRP_FRIENDLYNAME,
&dwPropType,
(LPBYTE)
szFriendlyName,
sizeof(szFriendlyName),
&dwReqSize);
hKey = SetupDiOpenDevRegKey(DeviceInfoSet,
&DeviceInfoData,
DICS_FLAG_GLOBAL,
0, DIREG_DEV, KEY_READ);
if (hKey) {
long lRet;
dwReqSize = sizeof(szPortName);
lRet = RegQueryValueEx(hKey,
_T("PortName"),
0,
&dwType,
(LPBYTE) & szPortName,
&dwReqSize);
RegCloseKey(hKey);
}
if (_strnicmp(szPortName, "COM", 3) == 0) { // Found COM port driver
int port = atoi(&szPortName[3]);
int i;
for (i = 0 ; i < comports ; i++) {
if (ComPortTable[i] == port) { // Confirm COM connection
ComPortDesc[i] = _strdup(szFriendlyName);
break;
}
}
}
}
}
cleanup:
SetupDiDestroyDeviceInfoList(DeviceInfoSet);
}
+-------------------------------------------------------+
|ttermpro.exe (filesys.cpp) |
+-------------------------------------------------------+
|ttpfile.dll (ttfile.c) |
+-------+--------+--------+--------+--------+-----------+
|Kermit | XMODEM | YMODEM | ZMODEM | B-Plus | Quick-VAN |
+-------+--------+--------+--------+--------+-----------+
For example, if you select to send a file via XMODEM, the process flow will be as follows.
filesys.cpp: OnFileXSend() -> XMODEMStart() -> OpenProtoDlg() -> ttfile.c: ProtoInit() -> xmodem.c: XInit()The processing of received file using ZMODEM is as follows.
filesys.cpp: OnFileZRcv() -> ZMODEMStart() -> OpenProtoDlg() -> ttfile.c: ProtoInit() -> zmodem.c: ZInit()
| Function | Meaning |
|---|---|
| XInit | Initialization |
| XSendPacket | File transmission |
| XReadPacket | File reception |
| XTimeOutProc | Timeout handling |
| XCancel | Cancellation |
| Function | Meaning |
|---|---|
| ZInit | Initialization |
| ZParse | File transmission |
| ZParse | File reception |
| ZTimeOutProc | Timeout handling |
| ZCancel | Cancellation |
Oct Dec Hex Char Oct Dec Hex Char ------------------------------------------------------------------------ 001 1 01 SOH (start of heading) 101 65 41 A 002 2 02 STX (start of text) 102 66 42 B 004 4 04 EOT (end of transmission) 104 68 44 D 006 6 06 ACK (acknowledge) 106 70 46 F 025 21 15 NAK (negative ack.) 125 85 55 U 030 24 18 CAN (cancel) 130 88 58 X
; XMODEM log XmodemLog=onSample log file where Tera Term (COM10) sends to RLogin (COM11) 67-byte long file using XMODEM protocol is shown below.
<<< 15 . >>> 01 01 FE 23 0D 0A 23 20 6B 6E 6F 77 6E 5F 68 6F ...#..# known_ho 73 74 73 20 66 69 6C 65 20 66 6F 72 20 54 54 53 sts file for TTS 53 48 28 41 6E 20 53 53 48 20 45 78 74 65 6E 73 SH(An SSH Extens 69 6F 6E 20 74 6F 20 54 65 72 61 20 54 65 72 6D ion to Tera Term 29 0D 0A 23 0D 0A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A )..#............ 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A ................ 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A ................ 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A ................ 1A 1A 1A EC .... <<< 06 . >>> 04 . <<< 06Step by step explanation of the above log:
<<<
15 .
>>>
01 01 FE 3B 20 73 61 6D 70 6C 65 20 6D 61 63 72 ...; sample macr
6F 20 6F 66 20 54 65 72 61 20 54 65 72 6D 0D 0A o of Tera Term..
3B 0D 0A 3B 20 46 69 6C 65 3A 20 73 63 72 65 65 ;..; File: scree
6E 63 61 70 74 75 72 65 2E 74 74 6C 0D 0A 3B 20 ncapture.ttl..;
44 65 73 63 72 69 70 74 69 6F 6E 3A 20 63 61 70 Description: cap
74 75 72 65 20 73 63 72 65 65 6E 20 63 6F 6E 74 ture screen cont
65 6E 74 73 20 61 6E 64 20 77 72 69 74 65 20 74 ents and write t
6F 20 66 69 6C 65 0D 0A 3B 20 45 6E 76 69 72 6F o file..; Enviro
6E 6D 65 F4 nme.
<<<
06 .
>>>
01 02 FD 6E 74 3A 20 67 65 6E 65 72 69 63 0D 0A ...nt: generic..
3B 20 55 70 64 61 74 65 3A 20 32 30 30 37 2F 31 ; Update: 2007/1
31 2F 32 35 2C 20 31 32 2F 35 2C 20 32 30 30 38 1/25, 12/5, 2008
2F 30 31 2F 33 30 0D 0A 3B 20 41 75 74 68 6F 72 /01/30..; Author
3A 20 49 57 41 4D 4F 54 4F 20 4B 6F 75 69 63 68 : IWAMOTO Kouich
69 20 28 64 6F 64 61 29 2C 20 59 75 74 61 6B 61 i (doda), Yutaka
20 48 69 72 61 74 61 0D 0A 3B 20 54 69 70 73 3A Hirata..; Tips:
0D 0A 3B 20 20 20 49 74 20 69 73 20 72 65 63 6F ..; It is reco
6D 6D 65 CA mme.
<<<
06 .
>>>
01 03 FC 6E 64 65 64 20 74 68 61 74 20 79 6F 75 ...nded that you
20 77 69 6C 6C 20 61 64 64 20 69 6E 20 74 68 65 will add in the
20 66 6F 6C 6C 6F 77 69 6E 67 20 65 6E 74 72 79 following entry
0D 0A 3B 20 20 20 69 6E 20 60 4B 45 59 42 4F 41 ..; in `KEYBOA
52 44 2E 43 4E 46 27 20 66 69 6C 65 20 62 65 63 RD.CNF' file bec
61 75 73 65 20 79 6F 75 20 63 61 6E 20 63 61 70 ause you can cap
74 75 72 65 20 79 6F 75 72 20 73 63 72 65 65 6E ture your screen
0D 0A 3B 20 20 20 61 74 20 6F 6E 65 27 73 20 66 ..; at one's f
69 6E 67 9C ing.
:
:
:
<<<
06 .
>>>
01 0E F1 73 70 72 69 6E 74 66 20 22 73 63 72 65 ...sprintf "scre
65 6E 63 61 70 74 75 72 65 5F 25 73 25 73 25 73 encapture_%s%s%s
2D 25 73 25 73 25 73 2E 74 78 74 22 20 44 61 74 -%s%s%s.txt" Dat
65 59 20 44 61 74 65 4D 20 44 61 74 65 44 20 54 eY DateM DateD T
69 6D 65 48 20 54 69 6D 65 4D 20 54 69 6D 65 53 imeH TimeM TimeS
0D 0A 66 69 6C 65 6E 61 6D 65 20 3D 20 69 6E 70 ..filename = inp
75 74 73 74 72 0D 0A 72 65 74 75 72 6E 0D 0A 1A utstr..return...
1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A ................
1A 1A 1A 75 ...u
<<<
06 .
>>>
04 .
<<<
06
; YMODEM log YmodemLog=onSample log file where Tera Term (COM10) sends to RLogin (COM11) 67-byte long file using YMODEM protocol is shown below.
<<< 43 C >>> 02 00 FF 73 73 68 5F 6B 6E 6F 77 6E 5F 68 6F 73 ...ssh_known_hos 74 73 00 36 37 20 31 31 31 36 32 32 30 30 31 30 ts.67 1116220010 30 20 31 30 30 36 34 34 00 00 00 00 00 00 00 00 0 100644........ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 1B 08 ..... <<< 06 43 .C >>> 02 01 FE 23 0D 0A 23 20 6B 6E 6F 77 6E 5F 68 6F ...#..# known_ho 73 74 73 20 66 69 6C 65 20 66 6F 72 20 54 54 53 sts file for TTS 53 48 28 41 6E 20 53 53 48 20 45 78 74 65 6E 73 SH(An SSH Extens 69 6F 6E 20 74 6F 20 54 65 72 61 20 54 65 72 6D ion to Tera Term 29 0D 0A 23 0D 0A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A )..#............ 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A ................ 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A ................ 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A ................ 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A ................ 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A ................ 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A ................ 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A ................ 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A ................ 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A ................ 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A ................ 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A ................ 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A ................ 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A ................ 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A ................ 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A ................ 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A ................ 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A ................ 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A ................ 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A ................ 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A ................ 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A ................ 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A ................ 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A ................ 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A ................ 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A ................ 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A ................ 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A ................ 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A ................ 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A ................ 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A ................ 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A ................ 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A ................ 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A ................ 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A ................ 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A ................ 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A ................ 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A ................ 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A ................ 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A ................ 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A ................ 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A ................ 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A ................ 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A ................ 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A ................ 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A ................ 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A ................ 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A ................ 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A ................ 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A ................ 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A ................ 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A ................ 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A ................ 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A ................ 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A ................ 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A ................ 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A ................ 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A ................ 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A ................ 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A 1A ................ 1A 1A 1A 6D 7A ...mz <<< 06 . >>> 04 . <<< 06 43 .C >>> 02 00 FF 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 ..... <<< 06Step by step explanation of the above log:
; Kermit log KmtLog=onKERMIT was initially designed for low speed connections that's why it could not send more than 94 bytes of data at a time. However, it now has extended option allowing to transmit several kilobytes of data if both - server and client can support this functionality.
Basic Kermit Packet Layout
|<------Included in CHECK------>|
| |
+------+-----+-----+------+------ - - -+-------+
| MARK | LEN | SEQ | TYPE | DATA | CHECK |<terminator>
+------+-----+-----+------+------ - - -+-------+
| |
|<--------LEN-32 characters------>|
MARK A real control character, usually Ctrl-A (0x01).
LEN One character, length of remainder of packet + 32, max 95. "LEN+2" is whole size.
SEQ One character, packet sequence number + 32, modulo 64. The number is from 0 to 63.
TYPE One character, an uppercase letter.
DATA Transmitted data
CHECK One, two or three bytes as negotiated.
<terminator> Any control character required for reading the packet.
Extended packet format is shown below.
Kermit Extended Packet Layout
|<-------------------------Included in CHECK------------->|
| |
|<-------Included in HCHECK------->| |
| | |
+------+-----+-----+------+-------+-------+--------+----- - - - -+-------+
| MARK | | SEQ | TYPE | LENX1 | LENX2 | HCHECK | DATA | CHECK |
+------+-----+-----+------+-------+-------+--------+----- - - - -+-------+
blank | |
|<------------------->|
LX1=LENX1-32, LX2=LX2-32 95 x LX1 + LX2 chars
HCHECK is a single-character type 1 checksum
In order to send more than 94 bytes of data, extended format's field containing data size is increased to two bytes. "LEN" is always zero of basic format (after adding 32 it is equal to ASCII code of whitespace character). Additionally, the size of the header increased by 3 bytes and header checksum was added.
Initialization String
1 2 3 4 5 6 7 8 9 10
+-------+-------+-------+-------+-------+-------+-------+-------+-------+- -
| MAXL | TIME | NPAD | PADC | EOL | QCTL | QBIN | CHKT | REPT |
+-------+-------+-------+-------+-------+-------+-------+-------+-------+- -
10 CAPAS+1 CAPAS+2 CAPAS+3
- --+-------+ - -+--------+--------+--------+- -
| CAPAS ... 0| WINDO | MAXLX1 | MAXLX1 |
- --+-------+- -+--------+--------+--------+- -
MAXL Maximum length (0-94) +32
TIME Timeout, seconds (0-94) +32
NPAD Number of pad characters (0-94) +32
EOL Packet terminator (0-63) +32
QCTL Control prefix, literal
QBIN 8th bit prefix, literal
CHKT Block check type {1,2,3}, literal
REPT Repeat count prefix, literal
CAPAS Extendable capabilities mask, ends when value-32 is even
WINDO Window size (0-31) +32
MAXLX1
High part of extended packet maximum length (int(max/95)+32)
MAXLX2
Low part of extended packet maximum length (mod(max,95)+32)
Below is the list of packet types.
Packet Types
Y Acknowledgment (ACK). Data according to what kind of packet is being acknowledged.
N Negative Acknowledgment (NAK). Data field always empty.
S Send Initiation. Data field contains unencoded initialization string. Tells receiver to expect files. ACK to this packet also contains unencoded initialization string.
I Initialize. Data field contains unencoded initialization string. Sent to server to set parameters prior to a command. ACK to this packet also contains unencoded initialization string.
F File Header. Indicates file data about to arrive for named file. Data field contains encoded file name. ACK to this packet may contain encoded name receiver will store file under.
X Text Header. Indicates screen data about to arrive. Data field contains encoded heading for display.
A File Attributes. Data field contains unencoded attributes. ACK may contain unencoded corresponding
agreement or refusal, per attribute.
D Data Packet. Data field contains encoded file or screen data. ACK may contain X to interrupt sending this file, Z to interrupt entire transaction.
Z End of file. Data field may contain D for Discard.
B Break transmission.
E Error. Data field contains encoded error message.
R Receive Initiate. Data field contains encoded file name.
C Host Command. Data field contains encoded command for host's command processor.
K Kermit Command. Data field contains encoded command for Kermit command processor.
T Timeout psuedopacket, for internal use.
Q Block check error psuedopacket, for internal use.
G Generic Kermit Command. Data field contains a single character subcommand, followed by zero or more
length-encoded operands, encoded after formation:
I Login [<%user[%password[%account]]>]
C CWD, Change Working Directory [<%directory[%password]>]
L Logout, Bye
F Finish (Shut down the server, but don't logout).
D Directory [<%filespec>]
U Disk Usage Query [<%area>]
E Erase (delete) <%filespec>
T Type <%filespec>
R Rename <%oldname%newname>
K Copy <%source%destination>
W Who's logged in? [<%user ID or network host[%options]>]
M Send a short Message <%destination%text>
H Help [<%topic>]
Q Server Status Query
P Program <%[program-filespec][%program-commands]>
J Journal <%command[%argument]>
V Variable <%command[%argument[%argument]]>